Configuring a custom domain for my serverless web app adds a level of professionalism and branding. By combining AWS Route 53 for DNS management with Azure CDN, I can serve my Azure-hosted content on a custom domain, enhancing accessibility and user experience. In this guide, I’ll go through the process of setting up a custom domain for Azure CDN using Route 53 and enabling SSL/TLS for secure connections. Terraform will be used to automate much of this setup, making it easily repeatable and scalable.
Step 1: Configuring Azure CDN with a Custom Domain
Azure CDN allows you to associate a custom domain with your CDN endpoint. This custom domain is where Route 53 will point traffic, allowing requests to reach your Azure-hosted static content.
Terraform Code - Azure CDN Custom Domain Setup
In this configuration, I define a custom domain for our CDN endpoint and configure SSL/TLS for secure communication.
resource "azurerm_cdn_profile" "this" {
name = local.project
location = azurerm_resource_group.this.location
resource_group_name = azurerm_resource_group.this.name
sku = var.cdn_profile_sku
}
resource "azurerm_cdn_endpoint" "this" {
name = local.project
profile_name = azurerm_cdn_profile.this.name
resource_group_name = azurerm_resource_group.this.name
origin {
name = "storageorigin"
host_name = azurerm_storage_account.this.primary_blob_host
}
is_compression_enabled = true
content_types_to_compress = ["text/html", "text/css", "application/javascript"]
is_http_allowed = false
is_https_allowed = true
}
resource "azurerm_cdn_endpoint_custom_domain" "this" {
name = replace(local.site_domain, ".", "-")
cdn_endpoint_id = azurerm_cdn_endpoint.this.id
host_name = local.site_domain
cdn_managed_https {
certificate_type = "Dedicated"
protocol_type = "ServerNameIndication"
tls_version = "TLS12"
}
}
In this code:
- azurerm_cdn_profile sets up a profile for our CDN with the specified SKU.
- azurerm_cdn_endpoint configures the CDN endpoint to serve content from our storage account.
- azurerm_cdn_endpoint_custom_domain associates the custom domain with the CDN endpoint and enables HTTPS with TLS 1.2.
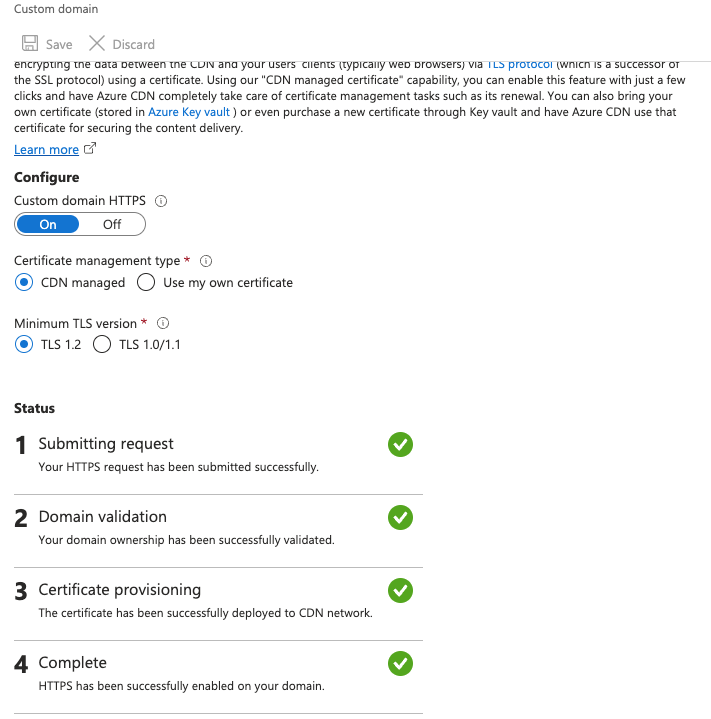
Step 2: Setting Up a CNAME Record in AWS Route 53
With Azure CDN configured, the next step is to direct traffic from my custom domain to the CDN endpoint using AWS Route 53. I’ll create a CNAME record in Route 53 to map the custom domain to the CDN endpoint.
Terraform Code - Route 53 CNAME Record Configuration
The following Terraform code sets up a CNAME record in Route 53 to point to the Azure CDN endpoint.
locals {
site_domain = "${local.project}.${var.public_domain}"
}
resource "aws_route53_record" "site" {
zone_id = data.aws_route53_zone.this.zone_id
name = local.site_domain
type = "CNAME"
ttl = 60
set_identifier = local.project
records = [azurerm_cdn_endpoint.this.fqdn]
weighted_routing_policy {
weight = 100
}
}
This code creates a CNAME record in the specified Route 53 hosted zone:
- zone_id specifies the hosted zone where the domain is managed.
- name is the custom domain.
- records points to the Azure CDN endpoint, effectively routing traffic to Azure.
Step 3: Validating DNS and SSL Configuration
After configuring both Azure CDN and Route 53, validate the setup by navigating to my custom domain in a web browser. The browser should display my Azure-hosted content with the secure HTTPS connection enabled.
I can use tools like dig or nslookup to verify that the CNAME record is correctly resolving to the Azure CDN endpoint.
Example Validation with dig
Run the following command to verify the CNAME record:
dig azure-serverless-site.brewsentry.com
Expected output:
- The response should show the CNAME record pointing to the Azure CDN endpoint.
- The connection should be secure (HTTPS) when accessed in a browser.
Configuring a custom domain with AWS Route 53 for an Azure CDN endpoint allows you to provide a seamless, branded experience for users accessing your serverless web app. With SSL/TLS enabled, you can ensure that all content is securely delivered over HTTPS. This setup, managed with Terraform, provides a streamlined and consistent way to deploy custom domains for Azure-hosted content.